A recent blog post described the phenomenon of the “Bow Wave” and its importance to Defense spending priorities. AMREL takes its responsibility of supplying mobile computing solutions to warfighters seriously, so we keep a close eye on how Defense allocates its resources.
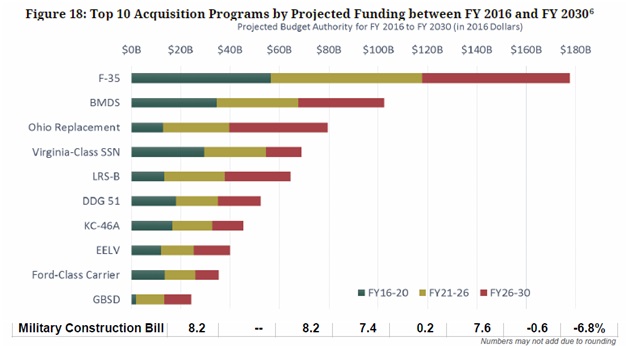
Under the “Bow Wave’s” influence, who are the winners and losers? Take a look at what the well-respected experts at the Center for Strategic and International Studies (CSIS) are predicting to be the top acquisition programs.
Defense Modernization Plans through 2020
A cursory analysis reveals that the Air Force, specifically aircraft acquisition (even more specifically the F-35) is the big “Bow Wave” winner.
“The Air Force is the largest contributor to the overall modernization Bow Wave. … funding for Air Force major acquisition programs is projected to grow by 73 percent in real terms from FY 2015 to its projected peak in FY 2023. This growth is driven primarily by aircraft programs. The Air Force’s three largest programs in terms of funding are the F-35A Joint Strike Fighter, Long Range Strike-Bomber (LRS-B), and KC- 46A aerial refueling tanker.”
Defense Modernization Plans through 2020
In spite of the presence of some big-ticket seafaring items on the above chart, the CSIS claims that the Navy and Marines do not much to look forward to in their future, at least according to a strict “Bow Wave’ analysis. However, I have doubts this will prove to be true. For one thing, they have plans:
“The Navy has been able to modernize by incorporating economically efficient capabilities, but much remains to be done. The sea service is making significant investments in aviation, he (Adm. Mulloy) noted, but it needs the RAQ-25 unmanned aerial vehicle quickly. Other critical capabilities include the SM-6, the LRASM, the HVP and maritime TACTOM.”
Signal
If things heat up in the South China Sea, I suspect the Navy won’t have any problems getting funding.
The CSIS analysis says that the Army will be another big winner.
“The Army’s budget for major acquisition programs is projected to increase 28 percent in real terms from FY 2015 to the peak in FY 2022. The Army’s plans indicate a significant Bow Wave in funding for ground systems…
“… the Army plans to ramp up funding for five major vehicle programs over the next five years… The largest of these programs is the Joint Light Tactical Vehicle (JLTV), a replacement for the Humvee. The program plans to reach full rate production of 2,200 vehicles per year by FY 2040. The Army is also developing the Armored Multi- Purpose Vehicle (AMPV), with low rate production planned to begin in FY 2020 and a total planned procurement of 2,897 vehicles. Programs are also planned to replace the Paladin self-propelled Howitzer, to upgrade Abrams tanks, and to modernize the fleet of Bradley Infantry Fighting Vehicles. Together these programs will increase funding for the Army’s major ground systems nearly threefold between FY 2015 an FY 2021.
“The Army has several modernization programs for communications systems planned as well. The Warfighter Information Network-Tactical (WIN-T) plans to continue fielding Increment 2 capabilities… The Army also plans to ramp up production of two variants of the Joint Tactical Radio System (JTRS): the Handheld, Manpack, and Small Form Fit (HMS radio and the Airborne, Maritime, and Fixed (AMF) radio. Having already experienced cost overruns, schedule slips, and many program changes, these three major Army communications programs are poised to more than double in funding between FY 2015 and FY 2021.”
Defense Modernization Plans through 2020
Then there are the non-service specific programs that can be expected to be well-funded. For example, cyber security will be favored in the budget process.
“Cyber right now is the cat’s meow—a notion sure to keep funding flowing for technological solutions, at least in the near term, to counter the emerging threats, according to Col. Gary Salmans, USAF, senior materiel leader of the Cryptologic and Cyber Systems Division within the Air Force Materiel Command.”
Signal
“President Barack Obama championed cybersecurity efforts Tuesday in seeking $19 billion for the cause as part of his fiscal year 2017 budget proposal. …The budget proposal for FY17, which begins October 1, is a 35 percent increase over the current fiscal year.”
Signal
Everybody loves SOCOM, so expect them to be eating steak, not hamburger. Space is being heavily militarized, so that’s another market Defense vendors should consider.
“In its enduring space race to narrow the materializing gap between the United States and peer competitors, the Air Force’s fiscal year 2017 budget emphasizes sustaining mission capabilities and improving space resilience by investing in command and control programs, situational awareness technologies, expendable launch systems and satellite communications.”
Signal
“U.S. officials to make recent bold leaps in their approaches, including establishing the Joint Interagency Combined Space Operations Center and making the Air Force secretary the principal DoD space adviser. With a goal to shift the Air Force’s space culture to one of warfighting, the center and the service secretary’s office will oversee a five-year, $5 billion budget increase for industry and allies to test new capabilities.”
Signal
If I wanted to pick the fattest single Defense target, I would say it was retrofitting.
“Upgrades and retrofits of existing programs appear to give the greatest number of opportunities for COTS systems. These are often replacing proprietary systems for more open standards that are ultimately easier and cheaper to maintain going forward.”
Robert Day, Vice President, Sales & Marketing, Lynx Software Technologies, Military Embedded Systems
The military can’t afford new stuff, so they want to make the old stuff last longer. At AMREL, we are very excited about this opportunity. Our platform flexibility, extensive technical support, and customization capabilities make us a very good fit for this. In fact, many of the programs favored by the “Bow Wave” (communication, vehicles, SOCOM, etc.) present excellent opportunities for us and our partners.
For over 30 years, AMREL has been proud to provide mobile computer solutions for American Defense needs. Whatever requirements arise, you can be sure that we will be there to meet them.